Nadezhda Kozhedub
UEFI firmware from five major vendors contain vulnerabilities that allow attackers with a foothold in a user’s network to infect connected devices with malware operating at the firmware level.
The vulnerabilities, which the researchers who discovered them called PixieFail, mostly pose a threat to public and private data centers and, of course, their users. People with minimal access to such a network – for example a paying customer, a low-level employee, or an attacker who has already gained limited access – could exploit the vulnerabilities to infect devices connected to a malicious UEFI. Short for Unified Extensible Firmware Interface, UEFI is a low-level, complex series of firmware responsible for the operation of almost every modern computer. By installing malicious firmware that runs before the main operating system loads, UEFI infections cannot be detected or removed using standard endpoint protections. They also provide unusually broad control over the infected device.
Five vendors and several customers were affected
The nine vulnerabilities that make up PixieFail are located in TianoCore EDK II, an open source implementation of the UEFI specification. Implementation is integrated into the offerings from Arm Ltd. Insyde, AMI, Phoenix Technologies, and Microsoft. The disadvantages lie in functionality related to IPv6, which is the successor to the IPv4 network address system. They can be exploited in what is known as a PXE, or Preboot Execution Environment, when configured to use IPv6.
PXE, sometimes colloquially referred to as Pixieboot or netboot, is a mechanism used by organizations to power large numbers of machines, which are often servers within large data centers. Instead of storing the operating system on the device during booting, PXE stores the image on a central server, known as the boot server. The booting devices determine the location of the boot server using the Dynamic Host Configuration Protocol and then send a request for the operating system image.
PXE is designed for ease of use, standardization, and quality assurance within data centers and cloud environments. When updating or reconfiguring the operating system, administrators only need to do it once and then ensure that hundreds or thousands of connected servers are running it every time they boot.
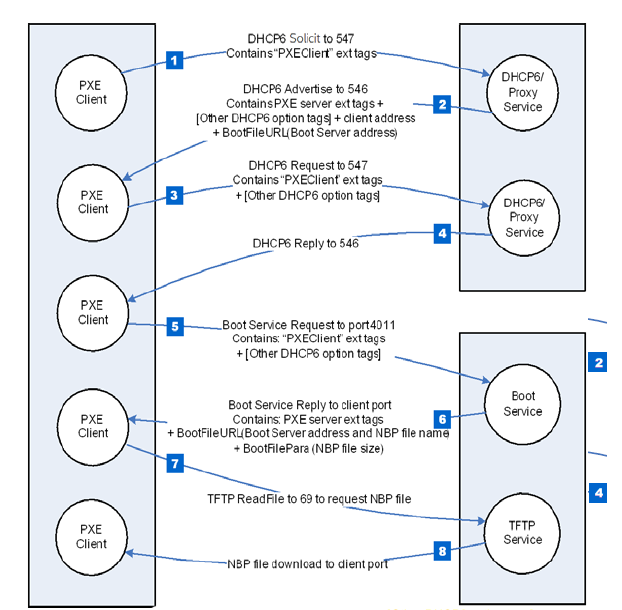
Diagram showing how PXE preamble works when using IPv6.
By exploiting the PixieFail vulnerabilities, an attacker can cause servers to download a malicious firmware image instead of the intended image. The malicious image in this scenario will create a permanent hotspot on the device installed before the operating system and any security software load which would typically indicate infections.
The vulnerabilities and proof-of-concept code demonstrating the existence of the vulnerabilities were developed by researchers from security firm Quarkslab, which published the results on Tuesday.
The network presence required to exploit most vulnerabilities is relatively small. Attackers do not need to create their own malicious server or obtain elevated privileges. Instead, the attacker only needs to be able to view and capture traffic as it traverses the local network. This type of access may be possible when someone has a legitimate account in a cloud service or after exploiting a separate vulnerability that grants limited rights to the system for the first time. An attacker could then exploit PixieFail to plant a UEFI-controlled backdoor into massive fleets of servers.
Quarkslab’s chief research officer, Ivan Arce, said in an interview:
The attacker does not need physical access to the client or boot server. The attacker only needs to have access to the network in which all these systems operate and must have the ability to capture packets and inject packets or send packets. When running a client-based server, an attacker only needs to send a malicious packet to the client in the response (request) that will trigger some of these vulnerabilities. The only access the attacker needs is network access, not physical access to any of the clients, nor to the boot server or DHCP server. Simply capture packets or send packets to the network, where all these servers operate.
For PixieFail to be exploited, PXE must be running. For the huge number of UEFI interfaces used, PXE does not work. PXE is generally only used in data centers and cloud environments to reboot thousands or tens of thousands of servers. Additionally, PXE must be configured to use it with IPv6 routing.